Exploring the intricate relationship between computer information systems and cybersecurity in organizations reveals a fascinating landscape of technological defenses and strategic implementations. As cyber threats continue to evolve, the role of these systems in protecting sensitive data and maintaining digital security becomes increasingly vital.
Let's delve into the dynamic world of cybersecurity supported by computer information systems.
Importance of Computer Information Systems in Cybersecurity
Computer information systems play a critical role in maintaining cybersecurity within organizations by providing the necessary tools and technologies to detect, prevent, and respond to cyber threats.
Detection of Cyber Threats
- Computer information systems utilize advanced monitoring and analytics tools to detect unusual activities or patterns that may indicate a potential cyber attack.
- These systems can track network traffic, log files, and user behavior to identify any anomalies that could pose a security risk.
- Examples of detection tools include intrusion detection systems (IDS), security information and event management (SIEM) software, and endpoint protection solutions.
Prevention of Cyber Attacks
- Computer information systems help organizations implement security measures such as firewalls, encryption, and access controls to prevent unauthorized access to sensitive data and systems.
- They can also enforce security policies and procedures to ensure that employees follow best practices for cybersecurity.
- By regularly updating software and patching vulnerabilities, computer information systems reduce the risk of successful cyber attacks.
Protection of Sensitive Data
- Computer information systems play a crucial role in safeguarding sensitive data, such as customer information, financial records, and intellectual property, from cyber threats.
- They can encrypt data at rest and in transit, ensuring that even if a breach occurs, the data remains secure and unreadable to unauthorized parties.
- Additionally, backup and recovery systems help organizations recover from cyber attacks and minimize the impact of data loss or disruption.
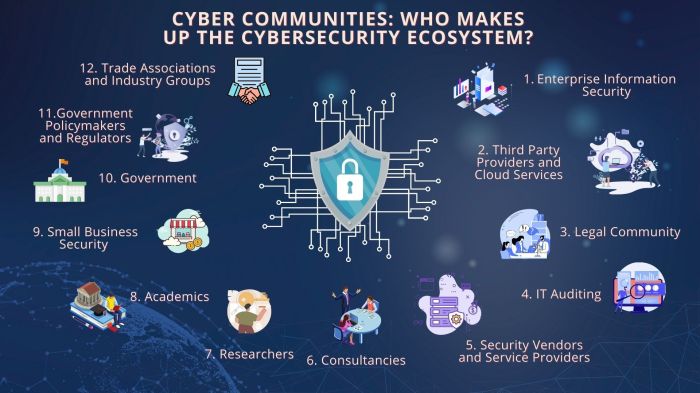
Components of Computer Information Systems for Cybersecurity
Computer information systems play a vital role in enhancing cybersecurity within organizations. Let's explore the key components that contribute to a robust cybersecurity framework.
Firewalls
Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They monitor and control incoming and outgoing network traffic based on predetermined security rules. By filtering out potentially harmful data packets, firewalls help prevent unauthorized access and cyber attacks.
Antivirus Software
Antivirus software is designed to detect, prevent, and remove malicious software, such as viruses, worms, and Trojan horses. It scans files and programs on a computer system for known patterns of malicious code, providing real-time protection against threats. Regular updates are essential to ensure antivirus software can effectively combat the latest malware threats.
Encryption Tools
Encryption tools are used to secure sensitive data by converting it into a coded format that can only be deciphered with the appropriate decryption key. This ensures that even if data is intercepted, it remains unreadable to unauthorized users. Encryption is crucial for protecting data both at rest and in transit, safeguarding it from potential breaches.
Intrusion Detection Systems
Intrusion detection systems (IDS) monitor network traffic for suspicious activity or potential security breaches. They analyze patterns and behaviors to identify anomalies that may indicate a cyber attack. IDS can be either network-based or host-based, providing organizations with real-time alerts and insights to respond swiftly to security incidents.
Security Information and Event Management Systems
Security information and event management (SIEM) systems collect and analyze log data from various sources within an organization's IT infrastructure. By correlating data and identifying patterns, SIEM systems enable organizations to proactively detect security incidents, prioritize threats, and respond effectively.
SIEM solutions play a crucial role in enhancing visibility, compliance, and incident response capabilities.
Integration of Computer Information Systems in Cybersecurity Strategies
Organizations integrate computer information systems into their overall cybersecurity strategies to ensure the protection of sensitive data and systems from cyber threats. By aligning IT infrastructure with cybersecurity objectives, organizations can enhance their security posture and reduce the risk of cyber attacks.
Examples of Integration
- Implementing firewalls, intrusion detection systems, and antivirus software to detect and prevent cyber threats.
- Integrating security information and event management (SIEM) systems to monitor network activity and identify potential security incidents.
- Utilizing encryption technologies to secure data at rest and in transit.
Importance of Continuous Monitoring and Updating
Continuous monitoring and updating of computer information systems are crucial for effective cybersecurity. Organizations need to regularly assess their systems for vulnerabilities and implement patches and updates to address potential security gaps. By staying proactive and vigilant, organizations can better protect their data and systems from evolving cyber threats.
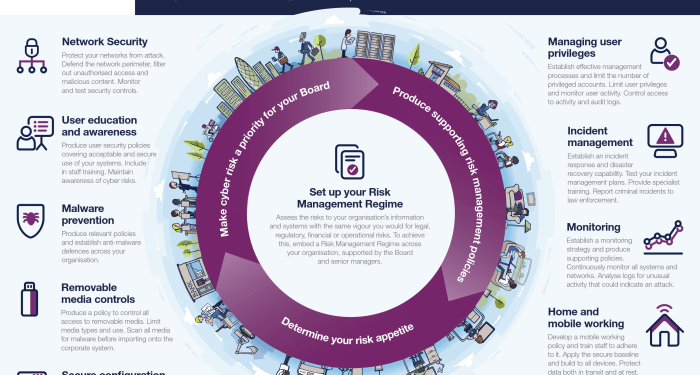
Challenges and Solutions in Using Computer Information Systems for Cybersecurity
Organizations face various challenges when leveraging computer information systems for cybersecurity. These challenges can hinder the effectiveness of security measures and put sensitive data at risk. However, there are solutions and best practices that organizations can implement to overcome these obstacles and enhance their cybersecurity posture.
Common Challenges Faced by Organizations
- Lack of skilled cybersecurity professionals: Many organizations struggle to find and retain qualified cybersecurity experts who can effectively manage and respond to security incidents.
- Complexity of IT infrastructure: The increasing complexity of IT environments makes it difficult to monitor and secure all network components effectively.
- Insufficient resources: Limited budgets and resources can hinder organizations from investing in advanced security technologies and tools.
- Adapting to evolving threats: Cyber threats are constantly evolving, and organizations may struggle to keep up with the latest attack vectors and vulnerabilities.
Solutions and Best Practices
- Invest in cybersecurity training and education: Organizations can provide training programs to upskill existing staff and attract new talent to address the skills gap.
- Implement automation and orchestration: Automation can help streamline security processes and improve response times to incidents, reducing the burden on cybersecurity teams.
- Adopt a risk-based approach: Prioritize security investments based on risk assessments to allocate resources effectively and protect critical assets.
- Enhance threat intelligence capabilities: Establishing robust threat intelligence programs can help organizations proactively identify and mitigate emerging threats.
Leveraging Advanced Computer Information Systems for Cybersecurity
- Implementing AI and machine learning: Advanced technologies like AI and machine learning can enhance threat detection and response capabilities, enabling organizations to stay ahead of cyber threats.
- Utilizing cloud-based security solutions: Cloud-based security tools offer scalability and flexibility to adapt to changing security needs and protect data across distributed environments.
- Integrating security into DevOps practices: DevSecOps approaches can help organizations build security into their development processes from the outset, improving overall security posture.
Concluding Remarks
In conclusion, the fusion of computer information systems with cybersecurity practices forms a formidable shield against digital threats, ensuring the resilience and integrity of organizational data. By understanding the importance of integrating these systems into cybersecurity strategies, organizations can proactively defend against cyber attacks and safeguard their digital assets.
Stay informed, stay secure.
FAQ Insights
How can computer information systems help organizations detect cyber threats?
Computer information systems utilize advanced monitoring tools and algorithms to detect unusual activities or patterns that may indicate a cyber threat. By analyzing network traffic and system logs, these systems can identify potential security breaches before they escalate.
What are the key components of computer information systems that enhance cybersecurity?
Key components include firewalls, antivirus software, encryption tools, intrusion detection systems, and security information and event management systems. Each plays a crucial role in fortifying the organization's defenses against cyber threats.
How do organizations ensure the continuous monitoring and updating of computer information systems for effective cybersecurity?
Organizations establish robust protocols for monitoring system performance, updating software patches regularly, and conducting security audits to ensure the integrity and effectiveness of their computer information systems. This proactive approach helps in staying ahead of potential vulnerabilities.



![20 Best Online Computer Information Systems Degrees [2025 CIS Degree Guide]](https://technology.fin.co.id/wp-content/uploads/2025/10/colleges-best_1910-120x86.png)

![Is Computer Information Systems a Good Major? [2025 Guide]](https://technology.fin.co.id/wp-content/uploads/2025/10/computer-information-systems-careers-2-120x86.jpg)